How To Find Ip Camera Address
How to detect IP cameras
Is it possible to observe surveillance cameras (CCTV, DVR, NVR, ANPR, Dome Camera, IP cameras, body cameras)?
If a photographic camera uses Wi-Fi, then its MAC address is visible to everyone. If you compare this MAC with the database of camera manufacturers, you lot can identify this photographic camera.
If a camera does not utilize Wi-Fi, but uses a wired network, then it can be detected only if you are connected to the same network (for instance, to the network of a hotel, airport, etc.).
If the device does non use a wired or wireless network, then the methods described below cannot detect such a device. That is, for instance, DVRs cannot be found in this mode.
For Wi-Fi devices, MAC addresses can be collected using Airodump-ng, for devices on the network to which we are connected, MAC addresses can be obtained using Nmap. Only we demand a database of surveillance/subconscious camera manufacturers, and cameras in general.
Related commodity: How to lookup MAC-address to find device manufacturer in Kali Linux
MAC accost database of all hidden cameras
I have not found any database of photographic camera manufacturers' MAC addresses other than small-scale lists put together by enthusiasts. Peradventure it would exist good for a starting betoken, but still non that I wish.
I institute a site that lists manufacturers of specialized equipment: https://directory.ifsecglobal.com/video-surveillance-code004812.html. I do not know if these lists are relevant or not, consummate or incomplete, but they are quite big and there are all manufacturers mentioned by enthusiasts (and those that are non on the site, I did not find them in the OUI list containing the MAC addresses of all device manufacturers).
The correct manufacturer proper noun tin be easily matched to the MAC database, so we only need to collect the vendor names – this is perfect for our purpose of finding surveillance/subconscious cameras.
Create a vendors.sh file:
gedit vendors.sh
Re-create the post-obit code into it:
#!/bin/bash TMP_FILE='/tmp/vendors.txt' FILE='vendors.txt' curl -south 'https://directory.ifsecglobal.com/screens-monitors-code004843.html' | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 's/">//' > $TMP_FILE for urlpath in cameras-code004815.html cctv-poles-and-columns-code004816.html cctv-poles-and-columns-code004816.html information-storage-solutions-code009685.html voice-video-integrated-information-systems-code004908.html dvr-code004822.html vocalisation-video-integrated-information-storage-code004941.html nvr-code004827.html 4k-cameras-code009684.html anpr-code004813.html trunk-worn-cameras-code007865.html hd-quality-cameras-code007866.html low-light-level-photographic camera-systems-code007867.html camera-housings-code004814.html internet-remote-surveillance-code004932.html cctv-monitoring-code004999.html dome-photographic camera-code004821.html ip-cameras-code004823.html security-camera-lenses-code004824.html security-monitors-code004825.html security-screens-code007437.html ptz-camera-code004828.html switches-code004968.html remote-surveillance-code004829.html public-space-surveillance-code005012.html infrared-cameras-code007439.html thermal-imaging-code004833.html ai-machinelearning-code009668.html security-cameras-code007485.html video-surveillance-code007482.html video-surveillance-code004812.html do curl -southward "https://directory.ifsecglobal.com/$urlpath" | grep -E 'ed-companyName' | grep -E -o '">[^/]+<' | sed 's/<//' | sed 'due south/">//' >> $TMP_FILE done #curl -due south '' | grep -Eastward 'ed-companyName' | grep -East -o '">[^/]+<' | sed 's/<//' | sed 'southward/">//' >> $TMP_FILE for letter in {A..Z} {two..v} {7..nine} do curl -s "https://www.ispyconnect.com/sources.aspx?letter=$letter of the alphabet" | grep -E -o 'man\.aspx\?n=[^"]{one,}"' | sed 's/homo.aspx?northward=//' | sed 's/"//' | while read -r line ; do grep -E "$line " vendors.txt >> $TMP_FILE washed done echo 'Tenda Technology Co., Ltd.' >> $TMP_FILE #https://www.google.com/search?q=Tenda+Technology+CCTV&tbm=isch repeat 'LG Innotek' >> $TMP_FILE #https://www.google.com/search?q=LG+Innotek+CCTV&tbm=isch echo 'Paw Held Products Inc' >> $TMP_FILE #Handheld Thermal Cameras echo 'Wistron Neweb Corporation' >> $TMP_FILE #https://www.wnc.com.tw/alphabetize.php?activeness=pro_detail&id=76 repeat 'HangZhou KuoHeng Technology Co.,ltd' >> $TMP_FILE #https://www.google.com/search?q=HangZhou+KuoHeng+Technology&tbm=isch echo 'VCS Video Communication Systems AG' >> $TMP_FILE echo 'D-Link International' >> $TMP_FILE echo 'Cisco-Linksys, LLC' >> $TMP_FILE echo 'ICP Internet Advice Payment AG' >> $TMP_FILE repeat 'Cathay Dragon Technology Limited' >> $TMP_FILE echo 'SAMSUNG TECHWIN CO.,LTD' >> $TMP_FILE echo 'Hanwha Techwin Security Vietnam' >> $TMP_FILE echo 'Beward R&D Co., Ltd.' >> $TMP_FILE echo 'Lorex Technology Inc.' >> $TMP_FILE repeat 'TP-LINK TECHNOLOGIES CO.,LTD.' >> $TMP_FILE echo 'ABUS Security-Center GmbH & Co. KG' >> $TMP_FILE repeat 'ACM Systems' >> $TMP_FILE repeat 'Aztech Electronics Pte Ltd' >> $TMP_FILE repeat 'Axium Technologies, Inc.' >> $TMP_FILE echo 'Ace Centrality Limited' >> $TMP_FILE #repeat '' >> $TMP_FILE repeat "Total vendors in the list: "`true cat $TMP_FILE | wc -fifty` cat $TMP_FILE | sort| uniq > $FILE echo "Unique vendors in the list: "`true cat $FILE | wc -l` Run like this:
bash ./vendors.sh
This will create a vendors.txt file.
Statistics:
Total vendors in the listing: 1665 Unique vendors in the list: 680
In full, 680 unique manufacturers were plant – this is quite a lot. If you know other lists or databases, then write in the comments – nosotros tin utilise them or add information from them. I do non know if "no proper noun" got here. On AliExpress, surveillance cameras are sold without a name on the example, without mentioning the manufacturer in the instructions and without mentioning it on the box (considering there is no box). If you have MAC addresses of such "no proper noun", so write them in the comments, nosotros can add them to the script to improve coverage.
You can likewise browse the list of vendors.txt and remove entries that you call up are unnecessary. For instance, I noticed that a lot of possible false positives are caused past "HUAWEI TECHNOLOGIES CO.,LTD", since this company also makes mobile phones (simply they do surveillance cameras as well: https://www.google.com/search?q=HUAWEI+CCTV&tbm=isch).
Wi-Fi subconscious camera scanner by MAC accost
Now that nosotros accept a database of subconscious camera manufacturers, we need to collect MAC addresses in the neighborhood.
I will use the tried and tested method described in the article "How to discover all Wi-Fi devices in the expanse?"
The following are the commands to start collecting information. If yous do not sympathise something about them, so refer to the commodity to which the link is given.
To parse the .csv file, you lot demand airodump-ng to create it. To do this, we set up the wireless card to monitor style. I e'er get-go with the following two commands so that no processes get in the way:
sudo systemctl stop NetworkManager sudo airmon-ng check impale
After that I set the Wi-Fi card into monitor mode:
sudo ip link ready wlan0 down sudo iw wlan0 set monitor control sudo ip link set wlan0 upward
At present we run airodump-ng with the post-obit command:
sudo airodump-ng --berlin 60000 -w /tmp/test wlan0
If you are also interested in the v GHz band and if your wireless bill of fare supports it, then you tin apply this control:
sudo airodump-ng --channel 1-13,36-165 --berlin 60000 -westward /tmp/test wlan0
I saved collected information to the file /domicile/mial/cameras-01.csv, I got 1600 lines there, of form, we won't analyze information technology manually:
cat /home/mial/cameras-01.csv | wc -l 1600
In general, we tin use the script from the article "How to find all Wi-Fi devices in the area?", Just calculation to it a check against the database of camera manufacturers. And this is exactly what nosotros volition do, but later. The signal is that the script works slowly with numerous entries.
Therefore, first we will utilise a lighter script that will simply bank check if there is a surveillance camera effectually. And if they are, so yous can run a heavier script to analyze which Access Points they are connected to.
Create fc.sh file:
gedit fc.sh
Copy the following code into information technology:
#!/bin/fustigate if [[ "$1" && -f "$1" ]]; then FILE="$1" else echo 'Specify the .csv file you desire to parse.'; echo 'Launch example:'; echo -due east "\tbash fc.sh /tmp/test-01.csv"; go out fi while read -r line ; do newline="$(echo $line | grep -E '([A-Z0-nine:]{17})')" if [ "$newline" ]; and so MAC2=`echo "$newline" | sed 'south/ //g' | sed 'due south/-//g' | sed 's/://g' | cutting -c1-6` resultshort="$(grep -i ^$MAC2 ./oui.txt)"; vendor=`echo "$resultshort" | cut -f 3` #vendor=`repeat "$resultshort" | awk -F '\t' '{impress $three}'` if [ "$vendor" ]; then result3=${vendor%,*} iscamera='' iscamera=`cat vendors.txt | grep -i "$result3"` if [ "$iscamera" ]; then echo echo $newline echo $vendor echo -e "\t\t\t\033[7mIt is likely a camera or other surveillance device\east[0m" echo fi fi fi done < <(grep -Due east '([A-Za-z0-nine._: @\(\)\\=\[\{\}\"%;-]+,){five} ([A-Z0-nine:]{17})|(not associated)' $FILE | awk -F ',' '{print $i}') Run like this:
bash ./fc.sh /PATH/TO/FILE.csv
If the file that I got from airodump-ng is located at /tmp/exam-01.csv then my command is every bit follows:
bash fc.sh /tmp/examination-01.csv
Nosotros besides need a file with a database of MAC addresses and their corresponding manufacturers, download information technology to the aforementioned directory where you placed the fc.sh file – yous demand to download this file before running fc.sh and all other scripts from this commodity:
wget http://standards-oui.ieee.org/oui/oui.txt
We fix the downloaded file, because it uses a DOS/Windows line break, and this leads to the problems, without this fix, the grep program could not observe the line, fifty-fifty if information technology matches the design:
dos2unix -i oui.txt
The script, using a database that maps manufacturers to their assigned MAC addresses (oui.txt), will determine the vendor name for each collected MAC address and then check if this vendor is present in the list of surveillance camera manufacturers.
The script will show the MAC address and manufacturer names for all potential cameras. If the script showed nothing, then nothing was found.
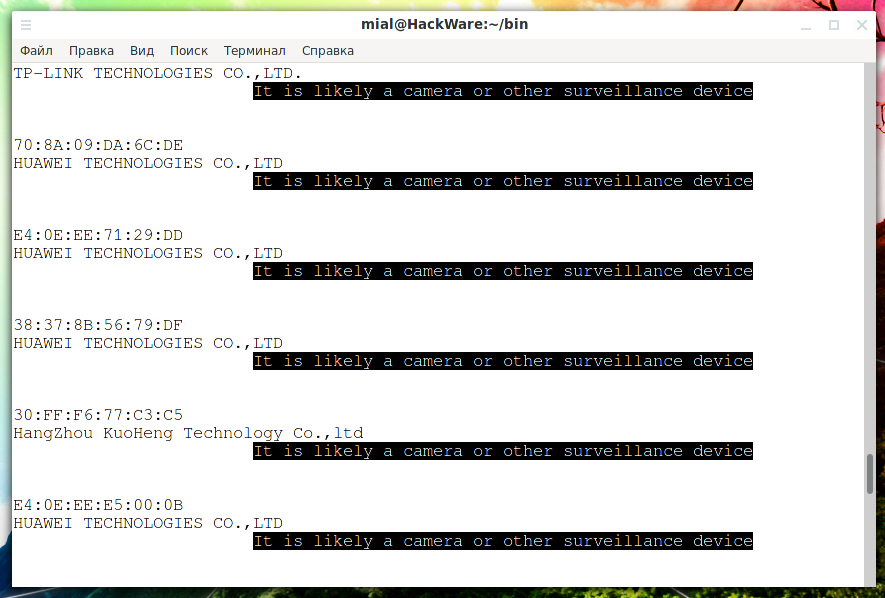
Think that some vendors produce non simply surveillance cameras, but besides a variety of other electronics (HUAWEI, Sony, Bosch), therefore, "faux positives" are very likely – devices can be assigned to "surveillance cameras", but actually they are not (for example, mobile HUAWEI phones). That is, if something was institute, or even if the script brought upwards a dozen devices, this does non hateful that these are all cameras. Starting time of all, pay attention to the manufacturer – quite often they are popular telephone manufacturers.
If you find something interesting, then you lot can use a script that shows which Access Points all devices are connected to.
Create findcameras.sh file:
gedit findcameras.sh
Copy the post-obit code into it:
#!/bin/fustigate if [[ "$one" && -f "$1" ]]; and then FILE="$one" else echo 'Specify the .csv file to clarify.'; echo 'Usage:'; echo -e "\tbash findcameras.sh /tmp/exam-01.csv"; get out fi echo -e "\033[1mTotal Admission Points: \033[0;31m`grep -East '([A-Za-z0-9._: @\(\)\\=\[\{\}\"%;-]+,){14}' $FILE | wc -fifty`\e[0m" echo -e "\033[1mTotal Stations: \033[0;31m`grep -E '([A-Za-z0-9._: @\(\)\\=\[\{\}\"%;-]+,){v} ([A-Z0-9:]{17})|(not associated)' $FILE | wc -l`\e[0m" repeat -e "\033[1mTotal Stations without association: \033[0;31m`grep -East '(non associated)' $FILE | wc -l`\east[0m" echo -e "\033[0;36m\033[1mAvailable Access Points:\east[0m" while read -r line ; do if [ "`echo "$line" | cut -d ',' -f 14`" != " " ]; then repeat -e "\033[1m" `repeat -e "$line" | cut -d ',' -f 14` "\due east[0m" else repeat -due east " \e[3mcould not become network proper noun (ESSID)\e[0m" fi fullMAC=`echo "$line" | cut -d ',' -f one` echo -eastward "\tMAC-address: $fullMAC" MAC=`echo "$fullMAC" | sed 's/ //m' | sed 'due south/-//g' | sed 's/://g' | cutting -c1-6` issue="$(grep -i -A 1 ^$MAC ./oui.txt)"; if [ "$effect" ]; then repeat -e "\tVendor: `echo "$result" | cut -f 3`" else echo -e "\tVendor: \eastward[3mInformation not found in the database.\e[0m" fi is5ghz=`repeat "$line" | cutting -d ',' -f iv | grep -i -Eastward '36|forty|44|48|52|56|60|64|100|104|108|112|116|120|124|128|132|136|140'` if [ "$is5ghz" ]; then echo -e "\t\033[0;31mIt operates at five GHz!\e[0m" fi printonce="\ttStations:" while read -r line2 ; do clientsMAC=`echo $line2 | grep -E "$fullMAC"` if [ "$clientsMAC" ]; then if [ "$printonce" ]; and so repeat -e $printonce printonce='' fi echo -due east "\t\t\033[0;32m" `echo $clientsMAC | cut -d ',' -f 1` "\east[0m" MAC2=`echo "$clientsMAC" | sed 'south/ //1000' | sed 's/-//g' | sed 'south/://grand' | cut -c1-6` result2="$(grep -i -A ane ^$MAC2 ./oui.txt)"; if [ "$result2" ]; and then echo -e "\t\t\tПроизводитель: `echo "$result2" | cut -f three`" ismobile=`echo $result2 | grep -i -East 'Olivetti|Sony|Mobile|Apple|Samsung|HUAWEI|Motorola|TCT|LG|Ragentek|Lenovo|Shenzhen|Intel|Xiaomi|zte|MEIZU'` warning=`repeat $result2 | grep -i -E 'ALFA|Intel'` if [ "$ismobile" ]; then echo -e "\t\t\t\033[0;33mThis is probably a mobile device\east[0m" fi if [ "$warning" ]; then repeat -e "\t\t\t\033[0;31;5;7mThe device can support the monitor style\e[0m" fi resultshort="$(grep -i ^$MAC2 ./oui.txt)"; vendor=`repeat "$resultshort" | cut -f 3` if [ "$vendor" ]; then result3=${vendor%,*} iscamera='' iscamera=`cat vendors.txt | grep -i "$result3"` if [ "$iscamera" ]; then echo -due east "\t\t\t\033[7mIt is probable a camera or other surveillance device\east[0m" fi fi else repeat -e "\t\t\tVendor: \e[3mInformation not constitute in the database.\e[0m" fi probed=`echo $line2 | cut -d ',' -f 7` if [ "`echo $probed | grep -East [A-Za-z0-9_\\-]+`" ]; so repeat -e "\t\t\tIt probed networks: $probed" fi fi done < <(grep -E '([A-Za-z0-ix._: @\(\)\\=\[\{\}\"%;-]+,){5} ([A-Z0-9:]{17})|(not associated)' $FILE) washed < <(grep -E '([A-Za-z0-9._: @\(\)\\=\[\{\}\"%;-]+,){14}' $FILE) echo -e "\033[0;36m\033[1mNot associated Stations:\east[0m" while read -r line2 ; practise clientsMAC=`repeat $line2 | cut -d ',' -f 1` repeat -e "\033[0;31m" `echo $clientsMAC | cut -d ',' -f 1` "\e[0m" MAC2=`repeat "$clientsMAC" | sed 'south/ //g' | sed 'southward/-//m' | sed 's/://g' | cut -c1-vi` result2="$(grep -i -A one ^$MAC2 ./oui.txt)"; if [ "$result2" ]; then repeat -east "\tVendor: `echo "$result2" | cut -f three`" ismobile=`repeat $result2 | grep -i -E 'Olivetti|Sony|Mobile|Apple|Samsung|HUAWEI|Motorola|TCT|LG|Ragentek|Lenovo|Shenzhen|Intel|Xiaomi|zte'` alarm=`echo $result2 | grep -i -Due east 'ALFA|Intel'` if [ "$ismobile" ]; then echo -east "\t\033[0;33mThis is probably a mobile device\east[0m" fi if [ "$warning" ]; then echo -e "\t\033[0;31;5;7mThe device can support the monitor mode\e[0m" fi resultshort="$(grep -i ^$MAC2 ./oui.txt)"; vendor=`repeat "$resultshort" | cut -f three` if [ "$vendor" ]; then result3=${vendor%,*} iscamera='' iscamera=`cat vendors.txt | grep -i "$result3"` if [ "$iscamera" ]; then repeat -e "\t\t\t\033[7mIt is likely a photographic camera or other surveillance device\eastward[0m" fi fi else echo -e "\tVendor: \e[3mInformation not constitute in the database.\e[0m" fi probed=`repeat $line2 | cutting -d ',' -f 7` if [ "`echo $probed | grep -Eastward [A-Za-z0-9_\\-]+`" ]; then echo -e "\tIt probed networks: $probed" fi done < <(grep -E '(not associated)' $FILE) Run like this:
fustigate findcameras.sh /PATH/TO/FILE.csv
For example:
bash findcameras.sh /tmp/test-01.csv
If yous await closely, you can come across that this is the wfw.sh script from the article about finding all Wi-Fi devices effectually yous, simply a check has been added to it against the listing of surveillance photographic camera manufacturers.
This script, like the previous ane, requires both oui.txt and vendors.txt files.
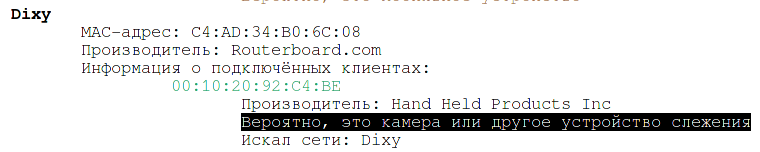
Hand Held Products Inc makes both thermal cameras and various barcode scanners, etc. - it can be whatsoever of these devices, since this is a shop'southward AP.
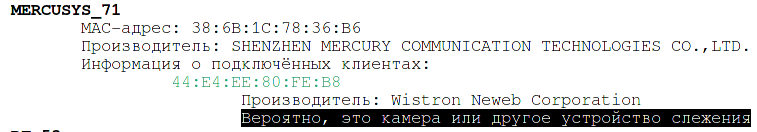
Wistron Neweb Corporation makes a variety of electronics, including Security IP Camera.
Instead of connecting via Wi-Fi, cameras can apply a wired network – such cameras volition not be included in the listing.
Searching for surveillance cameras in the local network
This method works only on networks where you can get the MAC addresses of other devices, that is, only on local networks. Scanning the Internet is useless. Examples of LANs that we oft connect to are public Wi-Fi hotspots at airports, hotels, restaurants, public transport, etc.).
Create fcl.sh file:
gedit fcl.sh
Copy the following code into it:
#!/bin/bash if [[ "$1" ]]; and then NET="$one" else echo 'Specify a subnet to search for surveillance cameras'; echo 'Usage example:'; echo -e "\tbash ./fcl.sh 192.168.0.0/24"; leave fi found=0 while read -r line ; do newline=$line if [ "$newline" ]; so MAC2=`echo "$newline" | sed 'due south/ //m' | sed 's/-//g' | sed 's/://yard' | cut -c1-vi` resultshort="$(grep -i ^$MAC2 ./oui.txt)"; vendor=`echo "$resultshort" | cut -f 3` if [ "$vendor" ]; so result3=${vendor%,*} iscamera='' iscamera=`cat vendors.txt | grep -i "$result3"` if [ "$iscamera" ]; then echo echo $newline echo $vendor echo -e "\t\t\t\033[7mIt is probable a camera or other surveillance device\e[0m" repeat establish=i fi fi fi done < <(sudo nmap -northward -sn -PR -PS -PA -PU -T5 $NET | grep -E -o '[A-Z0-nine:]{17}') if [ $found -eq i ]; then sudo nmap -A $NET fi Run like this (Nmap requires root privileges):
sudo bash fcl.sh NET/MASK
For example:
sudo bash ./fcl.sh 192.168.0.0/24
If devices with MAC addresses of surveillance camera manufacturers are found, they will be shown.
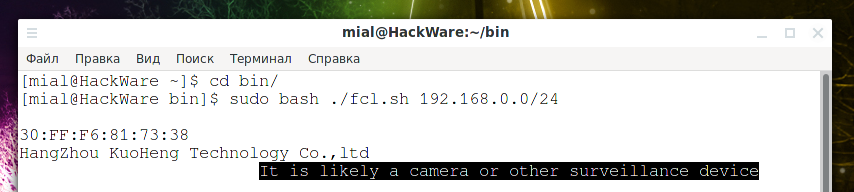
If null is shown, then goose egg was found.
If at to the lowest degree ane camera is found, another Nmap scan will be launched – more aggressive, with full output of the results so that you tin can run into the IP of the device, which may be a camera, as well as with an try to determine the version of the OS and services – this can help with identifying the camera.
Fragment of output from additional scan:
|_http-title: NETSurveillance WEB 554/tcp open rtsp H264DVR rtspd one.0 |_rtsp-methods: OPTIONS, DESCRIBE, SETUP, TEARDOWN, GET_PARAMETER, SET_PARAMETER, PLAY, PAUSE 8899/tcp open lather gSOAP 2.7 |_http-server-header: gSOAP/ii.7
The "NETSurveillance WEB" title hints that it is a network surveillance camera. Open ports 554 and 8899 belong to RTSP and ONVIF services specific to IP cameras.
Related article: IP Camera Security Audit
Search with DeviceManager (from python-dvr)
This method is just suitable if y'all are connected to the same local network equally the IP camera.
Programs for working with cameras must know their IP address. The normal user is non required to enter this accost manually. You might recollect that programs are scanning your local network, but this is unremarkably not the example. They actually transport specific hexadecimal data to the broadcast address. The data and port differ depending on the camera models. You can see an example of how this works in the article "Reverse applied science of network traffic".
DeviceManager programme (from python-dvr) can work with the post-obit groups of surveillance cameras:
- XM
- Dahua
- Fros
- Wans
- Beward
Nearly likely, this is not the manufacturer, simply the type of camera detection system used on the LAN. That is, if your photographic camera has a different manufacturer, DeviceManager can still find them.
To install and run DeviceManager, run the commands:
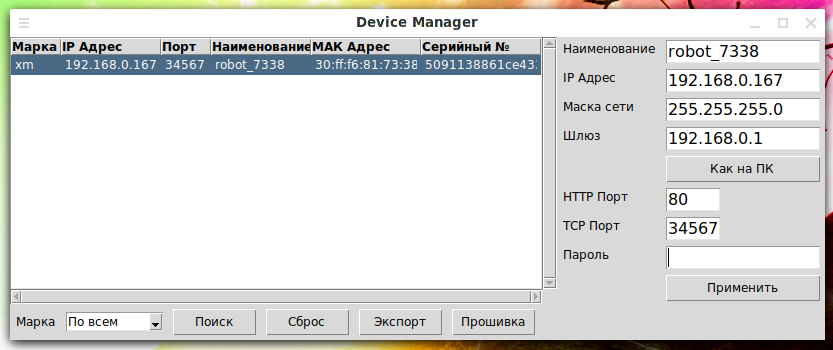
git clone https://github.com/NeiroNx/python-dvr cd python-dvr ./DeviceManager.py
A graphical interface will open, at that place it is plenty to click the Поиск ("Search") button.
Conclusion
The quality of scanning is primarily adamant past the quality of the list of manufacturers of surveillance cameras – if you know the better lists, write in the comments, I volition alter the instructions and scripts.
If you have examples of MAC addresses of surveillance cameras produced by "no name" and "Unbranded", then also write them in the comments – they can be added to scripts for additional verification by them.
Encounter also trackerjacker and "Wi-Fi device tracking". Using trackerjacker, you can too monitor wireless devices, for example, yous tin see when a Wi-Fi camera has started sending traffic – this may mean that the camera has noticed movement.
Another related article "How to perform selective jamming of Wi-Fi networks and clients (DoS attack on individual access points/clients)" (simply call back that cameras usually have retention cards inside to store video).
Detecting subconscious cameras by network traffic characteristics
When I already wrote this article and googled "mac addresses of subconscious cameras" to find at least something almost "Unbranded", considering hidden cameras are usually produced either without a make at all, or nether random names that are absent from the OUI, I stumbled upon a report "Detecting Subconscious Wireless Cameras through Network Traffic Assay". They were able to find patterns in the traffic characteristics of hidden cameras, although they did not share either the code or MAC addresses. Nevertheless, it may be interesting for someone to read it and push on new ideas.
Source: https://miloserdov.org/?p=5534
Posted by: daleytherning.blogspot.com


0 Response to "How To Find Ip Camera Address"
Post a Comment